LEAP Encryption Access Project
Bring back the 1990s!
What is Federation?
- user → provider → provider → user
- eg: SMTP, XMPP
Better federation
- The users should be protected from the provider.
- The provider should be protected from users.
Federation
is not dead
- Dissent - Provably anonymous group chat routing protocol - http://dedis.cs.yale.edu/dissent
- CONIKS - Privacy-preserving system for automatic key discovery and validation (it is like Certificate Transparency for user keys, but without the need for a gossip protocol) - http://eprint.iacr.org/2014/1004.pdf
What does
LEAP do?
-
LEAP Platform:
a toolkit to make it easy for you to run a service provider. -
New protocols:
so that users don't need to trust the provider. -
Bitmask client:
a client that works smoothly with any compatible provider.
LEAP Platform
sudo gem install leap_cli
leap new example --domain example.org
cd example
leap add-user --self
leap cert ca
leap cert dh
leap cert csr
leap node add blueberry services:openvpn \
ip_address:1.1.1.1 openvpn.gateway_address:1.1.1.2
leap node add raspberry services:couchdb,webapp \
ip_address:1.1.1.3
leap init node
leap deploy
New Protocols
- Soledad: searchable client-encrypted synchronized database.
- Bonafide: secure user registration, authentication, password change, etc.
- Key management: precise rules for OpenPGP best practices, automated.
Bitmask client
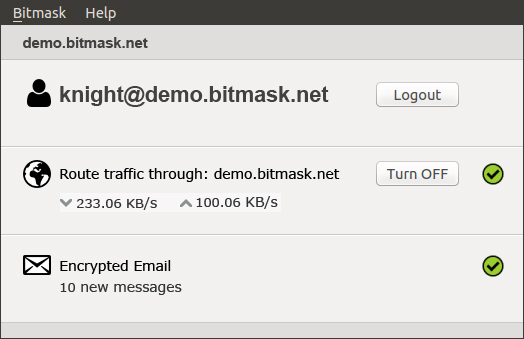
Example service: Email
We want all the features
- Easy to use.
- Backwards compatible with email and current OpenPGP usage.
- End-to-end encryption.
- Service provider has no access to user data.
- Automatic key discovery and validation.
- Strong protection for metadata, when supported.
- Cloud synchronized for high availability on multiple devices.
- No cleartext is ever written to disk.
- Fully searchable email.
- Work while offline, sync when network is available.
How?
Soledad: client-encrypted storage of content and metadata, searchable, offline support, backed up, sync'ed to multiple devices.
Invisible keys: let the robot manage keys; simple federated provider validation to start; forward compatibility with better validation as new protocols come online.
Tor: relay SMTP over hidden service when available (not in stable platform yet, but working live for two email providers).
Secure Remote Password: A login/password user experience, but the provider never has access to the password cleartext.
Infrastructure approaches:
- LEAP - SMTP & OpenPGP
- DIME - New protocols
- PPE - SMTP & S/MIME
Client approaches:
- Whiteout - Javascript client
- Mailpile - Python client
- e2e - Browser extension, from Google and Yahoo (maybe some infrastructure key validation in the future)
- Mailvelope - Browser extension
Our goals:
- increase the cost of dragnet surveillance
- mass adoption
Web Interface
- Potentially hosted by third party.
- Think "Bitmask client" but hosted in the cloud.
- Good looking.
- Search and tagging.
- Keys on the server, no browser crypto.
- LEAP Encryption Access Project @leapcode https://leap.se
- Bitmask App @bitmasknet https://bitmask.net
-
elijah@leap.se @ecsparrow
06A2 B8EE B5A4 E27D 3F57 14AC 544E E176 B3AE 7759
- Pixelated Project @pixelatedteam https://pixelated-project.org
-
team@pixelated-project.org
504A 14EA 39DE 1800 B676 9619 FF0E A8AE D649 7991