LEAP Encryption Access Project
Encryption should be
simple to provide and easy to use
- Tools for secure network communications
- Decentralization of service providers
Crypto is Hard
But wait, you said...
Encryption should be
simple to provide and easy to use
So...
Solve the Hard Problems
The “Big 7”
- Authenticity problem
- Meta-data problem
- Asynchronous problem
- Group problem
- Resource problem
- Availability problem
- Update problem
Authenticity problem
Public key validation is very difficult for users to manage, but without it you cannot have confidentiality
Meta-data problem
Existing protocols are vulnerable to meta-data analysis, even though meta-data is often much more sensitive than content
- Downgrade-proof DNSSEC/DANE
With one or more opportunistic schemes:
- Auto alias pairs
- Onion routing headers
- Third party dropbox
- Mixmaster with signatures
Asynchronous problem
For encrypted communication, you must currently choose between forward secrecy or the ability to communicate asynchronously
- OpenPGP vs. OTR
- Stop-gap: Layer forward secret transport atop OpenPGP
- Long term: Collaborate with others to create new encryption protocol standards
Group problem
In practice, people work in groups, but public key cryptography doesn’t
- First we...ummm
- Interesting work in secure file backup/sync/sharing (e.g. Wuala and SpiderOak)
- Proxy re-encryption
- Ring signatures
Resource problem
There are no open protocols to allow users to securely share a resource
- Yup, still got nothin' :/
- "Read-write-web", meet ["Group problem" solution here]
- Again, possibilities from file sync (Lazy Revocation and Key Regression)
Availability problem
People want to smoothly switch devices, and restore their data if they lose a device, but this very difficult to do securely
phew! we weren't out of ideas!
Update problem
Almost universally, software updates are done in ways that invite attacks and device compromises
So, what have you got?
Services
Encrypted Internet Proxy aka VPN
Chat (in progress)
Services in Planning
Client-Encrypted Filehosting
Voip
Collaborative Text Editor
For Users
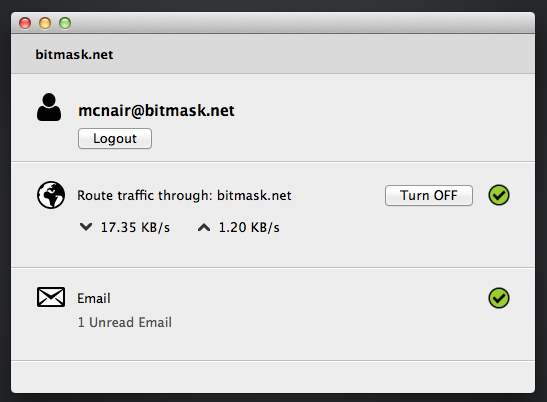
For Providers
- Automate Installation and Configuration of the services
- Secure Crypto presets (TLS parameters, etc)
leap-platform
Puppet recipes for configuring the server
# smtp TLS
postfix::config {
'smtp_use_tls': value => 'yes';
'smtp_tls_CApath': value => '/etc/ssl/certs/';
'smtp_tls_CAfile': value => $ca_path;
'smtp_tls_cert_file': value => $cert_path;
'smtp_tls_key_file': value => $key_path;
'smtp_tls_ask_ccert': value => 'yes';
'smtp_tls_loglevel': value => '1';
'smtp_tls_exclude_ciphers':
value => 'aNULL, MD5, DES';
# upstream default is md5 (since 2.5 and older used it), we force sha1
'smtp_tls_fingerprint_digest':
value => 'sha1';
'smtp_tls_session_cache_database':
value => 'btree:${queue_directory}/smtp_cache';
'smtp_tls_security_level':
value => 'may';
# see issue #4011
'smtp_tls_protocols':
value => '!SSLv2, !SSLv3';
}
Provider Config
Server Layout, IPs, contact details, etc
$ cat provider.json
//
// General service provider configuration.
//
{
"domain": "example.org",
"name": {
"en": "example"
},
"description": {
"en": "You really should change this text"
},
"contacts": {
"default": "admin@example.org"
},
"languages": ["en"],
"default_language": "en",
"enrollment_policy": "open"
}
$ cat nodes/web1.json
{
"ip_address": "99.231.92.23",
"services": "webapp",
"tags": "production"
}
Leap-cli
Command Line Tools for Admins
$ leap --yes deploy
Deploying to these nodes: web1, vpn1, couch1
= updated hiera/couch1.yaml
= updated hiera/web1.yaml
= checking node
- [web1] ok
- [couch1] ok
- [vpn1] ok
= synching configuration files
- hiera/web1.yaml -> web1:/etc/leap/hiera.yaml
- hiera/vpn1.yaml -> vpn1:/etc/leap/hiera.yaml
- hiera/couch1.yaml -> couch1:/etc/leap/hiera.yaml
- files/branding/tail.scss, files/branding/head.scss -> web1:/etc/leap
= synching puppet manifests
- /home/demo/leap/demo/leap_platform/[bin,puppet] -> web1:/srv/leap
- /home/demo/leap/demo/leap_platform/[bin,puppet] -> vpn1:/srv/leap
- /home/demo/leap/demo/leap_platform/[bin,puppet] -> couch1:/srv/leap
...
Setting up a new Provider
Initializing and deploying nodes
Provider Online
demo.bitmask.net - Reference Provider of LEAP
already open for beta testers
Interested Providers
Etc
Website: https://leap.se
Github Mirror: https://github.com/leapcode
Made with reveal.js