LEAP Encryption Access Project
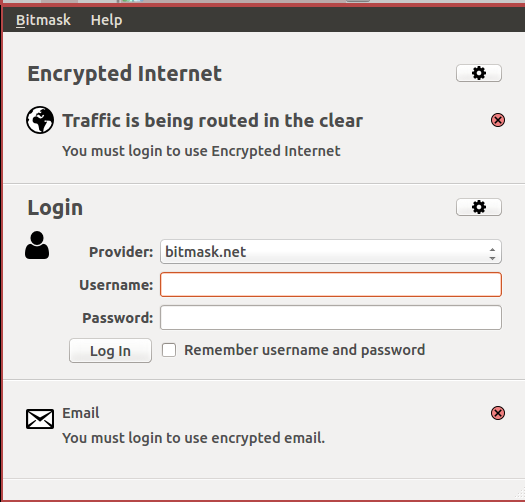
Für User
Für Provider
- Automatisierung Installation und Konfiguration der Dienste
- Sichere Crypto-Voreinstellungen (TLS Parameter, etc)
leap-platform
# smtp TLS
postfix::config {
'smtp_use_tls': value => 'yes';
'smtp_tls_CApath': value => '/etc/ssl/certs/';
'smtp_tls_CAfile': value => $ca_path;
'smtp_tls_cert_file': value => $cert_path;
'smtp_tls_key_file': value => $key_path;
'smtp_tls_ask_ccert': value => 'yes';
'smtp_tls_loglevel': value => '1';
'smtp_tls_exclude_ciphers':
value => 'aNULL, MD5, DES';
# upstream default is md5 (since 2.5 and older used it), we force sha1
'smtp_tls_fingerprint_digest':
value => 'sha1';
'smtp_tls_session_cache_database':
value => 'btree:${queue_directory}/smtp_cache';
'smtp_tls_security_level':
value => 'may';
# see issue #4011
'smtp_tls_protocols':
value => '!SSLv2, !SSLv3';
}
Provider Config
$ cat provider.json
//
// General service provider configuration.
//
{
"domain": "example.org",
"name": {
"en": "example"
},
"description": {
"en": "You really should change this text"
},
"contacts": {
"default": "admin@example.org"
},
"languages": ["en"],
"default_language": "en",
"enrollment_policy": "open"
}
$ cat nodes/web1.json
{
"ip_address": "99.231.92.23",
"services": "webapp",
"tags": "production"
}
Leap-cli
$ leap --yes deploy
Deploying to these nodes: web1, vpn1, couch1
= updated hiera/couch1.yaml
= updated hiera/web1.yaml
= checking node
- [web1] ok
- [couch1] ok
- [vpn1] ok
= synching configuration files
- hiera/web1.yaml -> web1:/etc/leap/hiera.yaml
- hiera/vpn1.yaml -> vpn1:/etc/leap/hiera.yaml
- hiera/couch1.yaml -> couch1:/etc/leap/hiera.yaml
- files/branding/tail.scss, files/branding/head.scss -> web1:/etc/leap
= synching puppet manifests
- /home/demo/leap/demo/leap_platform/[bin,puppet] -> web1:/srv/leap
- /home/demo/leap/demo/leap_platform/[bin,puppet] -> vpn1:/srv/leap
- /home/demo/leap/demo/leap_platform/[bin,puppet] -> couch1:/srv/leap
...
Leap-cli Screencasts
Dienste
Encrypted Internet Proxy aka VPN
Chat (in Arbeit)
Dienste in Planung
Client-encrypted Filehosting
Voip
Kollaborativer Texteditor